
Anyone
Can learn (IT/Non IT)
🚀 Get at ₹5,999 | Ethical Hacking with AI – Limited Time Offer!
Get 100% practical, hands-on training along with career guidance.
Can learn (IT/Non IT)
Course Rating
Learners
Free Doubt Sessions
Payment
Content Duration
Language
By Industry Experts
Hacking, hacker, types of hacker
Hackers and cybersecurity
Motto of cybersecurity (CIA triad)
Introduction to Linux (setup Kali Linux)
Linux commands
File system
sudoers file
Permissions (SUID)
Intro to Networking
3-way handshake
OSI model
Ports and protocols
Wi-Fi hacking PMKID attack (sample .cap files to crack)
Wi-Fi hacking — stealing saved passwords
Wi-Fi hacking with social engineering”
What is application version → update, bug fix
GHDB
Scanning the network (nmap)
Online Session 1
Vulnerability exploitation (version and Metasploit)
Malware and applications
Types of malware
Malware in action (MalwareBazaar)
Sandboxie Plus
Intro to Android pentesting: malware exploitation
Crax RAT
Port-forwarding with Telebit
Intro to Registry
The game of Registry: hide programs, turn- off
firewall, change process name,
MAC address spoofing”
Vulnerability exploitation (version and Metasploit)
Bat2exe compile and bypass the
Windows firewall
Vulnerability exploitation (version and Metasploit)
The game of Registry: hide programs, turn- off
firewall, change process name,
PS2EXE
MITM attack with Ettercap
MITM & Wireshark
DHCP Starvation attacks
LLMNR poisoning attack
What is Cryptography
Types (Encryption, Encoding and Hashing)
Online Session 2|
Cracking the Windows login screen hash
Crack passwords of password-protected files
Hashcat: the most powerful password cracker
Intro to OSINT (Ethical HackingToolkit)
Find info about (person, company)
reverse image lookup
What is Dark-web (Surface web / Deep web / Dark web)
Access Dark-web safely
Dark-web search engines
Using dark-web network for anonymity
What is phishing
Phishing frameworks 101
Phishing with EDEN
Manually performing phishing of a login page
Advanced Phishing with EvilnoVNC
Hashcat: the most powerful password cracker
What is Social Engineering
Why social engineering is the most
powerful attack
SET attacks



He is a passionate cybersecurity enthusiast who started his journey at 15 and has since trained over 5,000 students & professionals. With a community of 100,000+ followers on Instagram, he is recognized for making cybersecurity practical and engaging. His expertise includes Linux, Bug Bounty, Malware Development, and Black Hat Python.

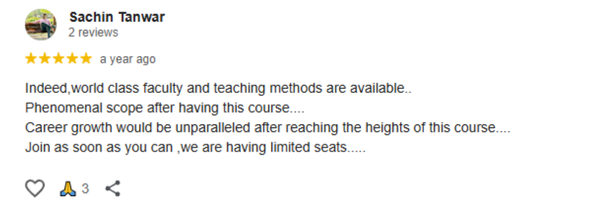
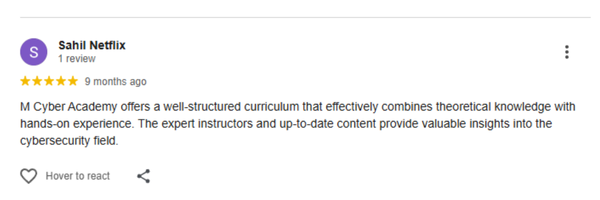
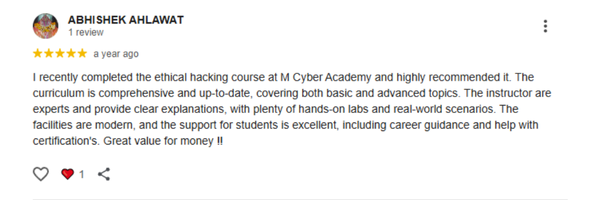
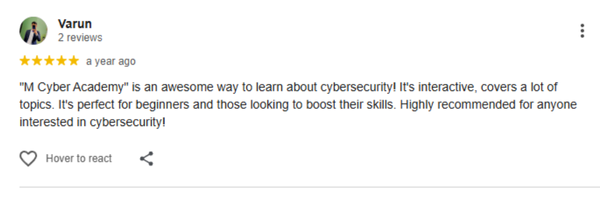

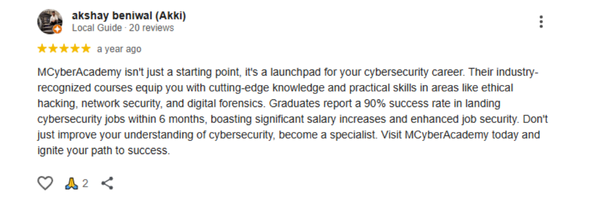
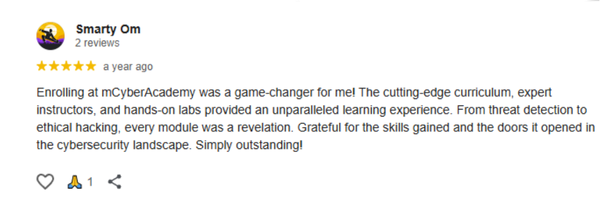
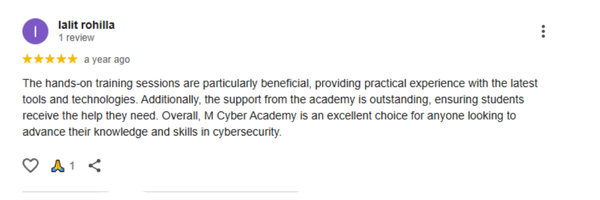
Our last batch of students truly enjoyed the Ethical Hacking with AI Live Course, gaining hands-on skills and practical experience. Their feedback reflects how engaging, practical, and career-boosting the training was.



This course combines traditional ethical hacking skills with the latest Artificial Intelligence (AI) tools and techniques. You’ll learn penetration testing, vulnerability assessment, and threat analysis while using AI-driven tools to automate security tasks and boost efficiency.
Anyone passionate about cybersecurity — whether a beginner, IT student, developer, or working professional. No prior hacking experience is required; basic computer knowledge is enough.
Unlike traditional courses, this one integrates AI and machine learning applications in cybersecurity, including automated reconnaissance, threat prediction, and malware detection. It’s also 100% hands-on with live labs and CTF challenges.
Yes. You’ll receive a certificate from M Cyber Academy, verifying your successful completion of the course and showcasing your expertise in Ethical Hacking & AI Security.
Absolutely. The course is designed for beginners to advanced learners. Each module builds step by step — starting from basic networking to advanced AI-powered hacking tools.
M Cyber Academy is India’s leading Ethical Hacking and Cybersecurity Training Institute. We empower learners with practical, hands-on training in Ethical Hacking, AI Security, Penetration Testing, and Digital Forensics. Our goal is to create the next generation of cybersecurity experts ready to secure the digital world.
Copyright © 2023. Maharaj Cybersecurity Pvt Ltd. All Rights Reserved